In This Article
Let’s explore this guide to understand the vitality of the data masking process and how you can do that in detail.
What is Data Masking?
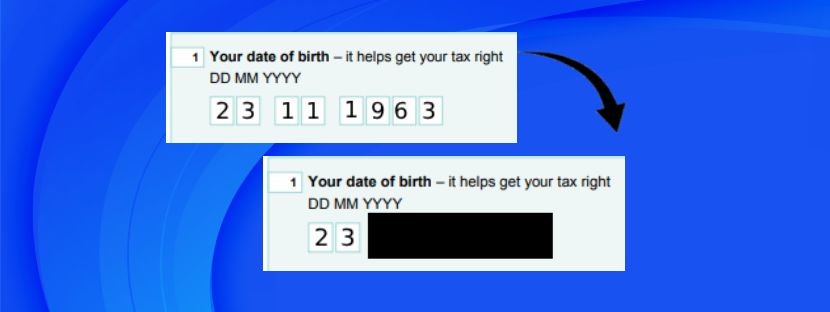
The process of creating similar-looking data but hiding all original information is called data masking. Masked information has various uses, including training users, testing software, and so many. So, the main aim of data masking is to create a replica of the data without revealing the real data.
Sometimes sharing information with third parties becomes vital for meeting different purposes. There’s where data is put at risk and it might invite complicated data breaching incidents. Therefore, securing the data while sharing it needs solid protection. That’s where data masking comes in, which emulates the original data.
Not only one way, rather, there are many ways we can mask data. For example;
Why Data Masking?
Adding extra security measures to your data through data masking while sharing it with third parties. But, that’s not what actually represents data masking. Let’s dig into the importance of masking more in detail.
Prevent Data Breach
Incidents of data breaches mostly happen because data owners often unwillingly share data access. The medium of data access, in most cases, is unencrypted data. Using that data, the malicious actor enters the database and copies the entire data. However, when you mask your data, no such incident will ever happen.
Internal Threat
Internal team members with malicious intent can harm your organization from the inside. They can leak your data, sell your business data to your competitors, or do any activity that can make your organization lose. Hence, to save your organization’s data from potential threats, you must mask your data. Even if your employees work with your data they’d never get all the details, except essential information. So, it can minimize internal data threats strategically.
Protect Production Database
Malicious elements can reach up to your production data if they find any trace. Thus, protecting your production database with data masking techniques is crucial here. It will prevent illegitimate access to your production database and protect it completely.
Data Compliance
As per the General Data Protection Regulation (GDPR), you need to make necessary arrangements to ensure the security of your data. Through masking the data, you can easily comply with the regulation. Thus, you can easily avoid legal complexities if your organization uses data masking to protect data.
Use of Data Masking Methods
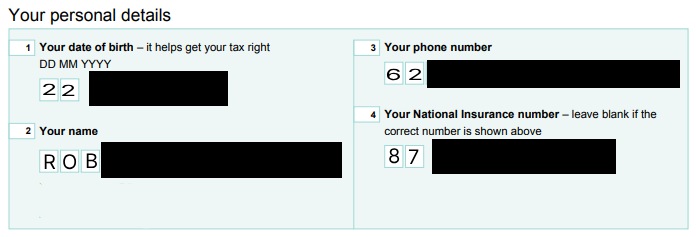
Card Information Received
Card Information Masked

Data Masking Challenges
As we’ve seen there are many ways of masking sensitive data, similarly, there are a lot of challenges involved in it also. Let’s discuss them one after another.
Format Replication
Masked data only remains useful when it follows the same format as its original dataset. Little changes made in the format can make the data unuseful. But, it’s the most common mistake that often happens due to a lack of technical expertise.
Data Integrity
Missing data in the database is a serious issue and that cannot be replaced with any data to mask it up. Proper knowledge about the process is the key here to maintaining data integrity across platforms.
Semantic Integrity
All data must fall under a certain range, otherwise it’ll create a mishap. Suppose in the age column of your database your pur random ages. For example, you put somewhere 18 while at another place you put 98. So, is the data range correct? Certainly not. You need to maintain semantic integrity while masking data.
Value Hide
Creating a replica of the original data is a tough process when it comes to hiding the data. Without proper knowledge, you might end up hiding all the data so it becomes hard to trace. Some information such as geographic details, the last few digits of cards, etc must be there.
Best Practices of Data Masking (Data Masking Techniques)
To avoid mistakes and errors in the masking process, you need to follow certain rules and techniques. Some best practices to mask data are;
Final Words
Hiding sensitive details while sharing data is not a compulsory thing rather it’s mandatory. It can help you from data breaches and security threats. With the help of a data masking service provider, you can easily do that. Added to that, you can tweak your requirements as well to get better results on your data operations.